You find here the most recent version of the Application Security poster. It comes in 3 sizes (A3, A2 and A1). A2 size is probably best suited for a discussion at the desk. A3 size is still workable but you need a good printer for the fine print (and a good vision, too). The A1 version is for the main purpose of a poster; hanging at a wall.
The poster is strictly product neutral and published under a Creative Commons license for better sharing (CC Attribution-NonCommercial-NoDerivates 4.0). Contact Acrosec Inc. if you would like to license it for rebranding or for other commercial purposes.
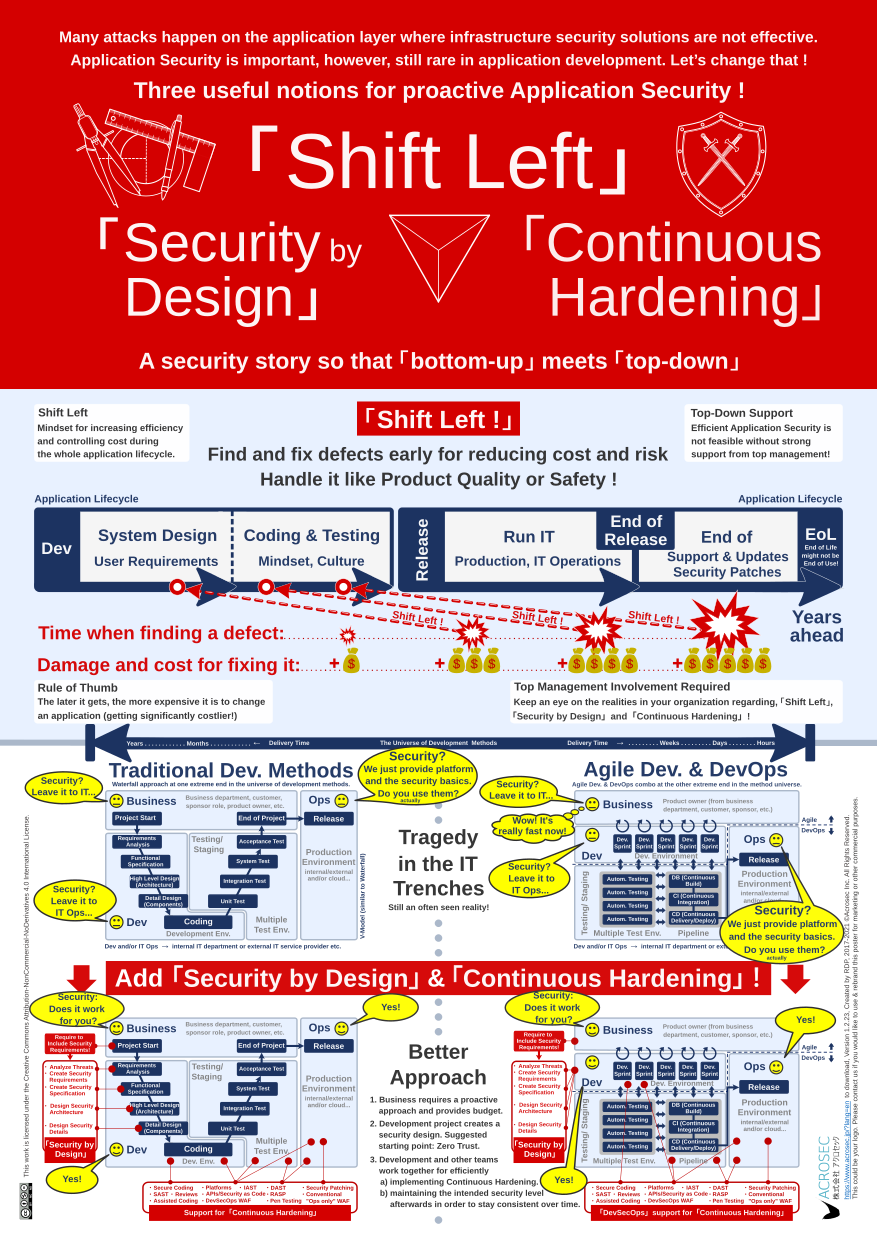
The purpose of this poster is to provide food for thought when discussing Application Security.
Download the “Continuous Hardening” Version
- Download as A3 sized poster (small)
- Download as A2 sized poster (medium)
- Download as A1 sized poster (large)
The overarching theme is about discussing the most important drivers which foster or inhibit the propagation of proactive security. It’s not about specific security technologies but about what makes people and organizations tick when it comes to development and Application Security.
Many attacks happen on the application layer where network or infrastructure security solutions are less or not effective. However, the majority of cybersecurity effort does not happen during application development. Why is that so, and what needs to change to advance Application Security?
The Application Security poster is an attempt to promote the three essential elements for improving Application Security. “Shift Left” is especially useful at the senior management level, while “Security by Design” and “Continuous Hardening” relate to concrete actions and tools in the IT trenches.
Intended Audience
The intended audience is twofold: “Top down” C-suite stakeholders and “bottom up” technology stakeholders from the ground in the IT trenches (developers, testers, operations, project and IT managers, but also people from Infosec, IT Risk, and IT Governance).
A CEO who is successful in the IT industry is probably already familiar with about 80% of this poster. The same should be said for experienced IT personnel, so we have a large overlap that can be useful.
Hopefully, your organization has already moved beyond the tragedy in the IT trenches situation and is doing proactive security. However, regardless of where you are within your organization, Application Security is notoriously difficult and tends to focus on many technical details.
Take the famous OWASP Top 10 list of vulnerabilities. It is essential, but certainly not an area where senior management can contribute. However, it should concern senior management why the current OWASP Top 10 looks awfully like the version from ten years ago, or even when it came first out in 2003. What are the mechanisms in many organizations that lead to the impression that we don’t really advance here? What are the root causes? What needs to change to make progress in Application Security?
IT Security is a complex topic with the tendency for endless technical detail discussions and a lot of finger-pointing. It helps to have a common language and various perspectives from management and technology insiders to guide anyone with the desire to understand, discuss, and improve the state of Application Security within the organization.
A good CEO would certainly want to understand the realities in the IT trenches if he/she perceives that Application Security might be important, especially if there is potential for repercussions on the business strategy. The purpose of this poster is that “top-down” and “bottom-up” stakeholders could have a more focused discussion if they use it as a mental guide when discussing the most important mechanisms for making or breaking Application Security within their organization.
Note:
Another version of this poster has been created to promote DevSecOps and to include different views from this perspective in relation to Continuous Hardening. See See “Narrow DevSecOps” vs. “Open DevSecOps”: Which camp are you in?
Author: Roberto Di Paolo
2017~2023 ©ACROSEC Inc., All Rights Reserved.
Last update 2021/9/17: Update to poster version 1.2.23
